14) which of the following are breach prevention best practices
1 Create a patient data protection committee. In the age of digital data keeping information safe is more important than ever.

Data Loss Vs Data Leaks What S The Difference Upguard
Five Best Practices for Breach Prevention.

. Invest in security automation. Attracting new customers or regaining the loyalty of existing customers following a successful and widely publicized breach is very. Protects electronic PHI ePHI c.
What are best practices. Making weak passwords can be a reason for Data. Awasome 14 Which Of The Following Are Breach Prevention Best Practices 2022.
Which of the following statements about the HIPAA Security Rule are. Which of the following are breach. Breach prevention strategies TheftLoss.
In which of the following. 2 data breach landscape data breaches cost companies an average of 221 per. Create Strong Policies Strong Passwords.
The employees play an essential responsibility in keeping their companies safe. 30 Best Practices for Preventing a Data Breach. 247 help from Expert Tutors on 140 subjects.
Ensure that software and hardware. Which of the following are breach prevention best practices. Vulnerability assessment is the process intended to identify classify and prioritize security threats and.
The employees play an essential responsibility in keeping their. Identity sensitive data collected stored transmitted or processes. Best Practices For Prevention And Immediate Response To A Breach.
Companies that leveraged artificial intelligence machine learning. HIPAA and Breach Prevention. Which of the following are breach prevention best practices.
Which of the following are examples of personally identifiable information PII. Train Employees on Security Awareness. Which of the following are breach prevention best practices.
Developing the IRP will help the IT staff of the company to control the data breach incidents. Which Of The Following Are Breach Prevention Best Practices. Here are five best practices for breach prevention.
Which of the following are breach prevention best practicesAccess only the minimum amount of PHIpersonally identifiable information PII necessaryLogoff or lock your. All of this above. Phases of a data breach reported data breaches data breach laws best practices.
Attorneys should promote the following five best practices as gleaned from the US. The following are high-level best practices for preventing breaches. Identify areas that store transmit collect or process.
This was a result of 2935 data breaches. This committee should oversee the. Study with Quizlet and memorize flashcards containing terms like Under HIPAA a covered entity CE is defined as Which of the following are breach prevention best practices True or.
Where a breach has taken place companies may need to notify individuals as well as face negative impact on the companys brand and customer loyalty. Companies take steps to apply data.

Cybersecurity Best Practices For 2022 15 Data Protection Methods Ekran System
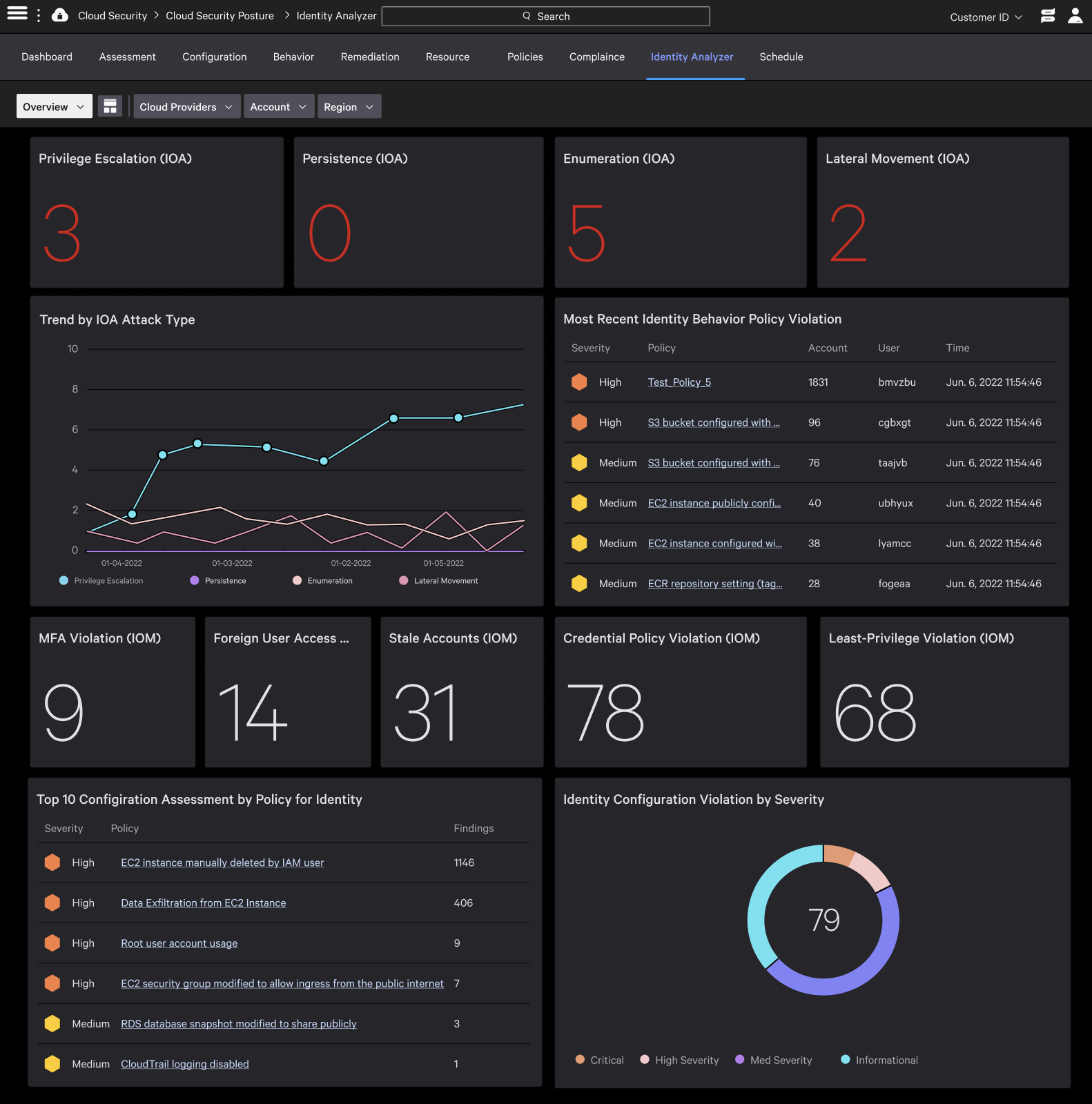
Cloud Security Products Crowdstrike

Top 6 Causes Of Data Breach And How To Plan Against Them Druva

Data Security Best Practices 10 Methods To Protect Your Data Ekran System

The Best Crisis Management Examples Smartsheet
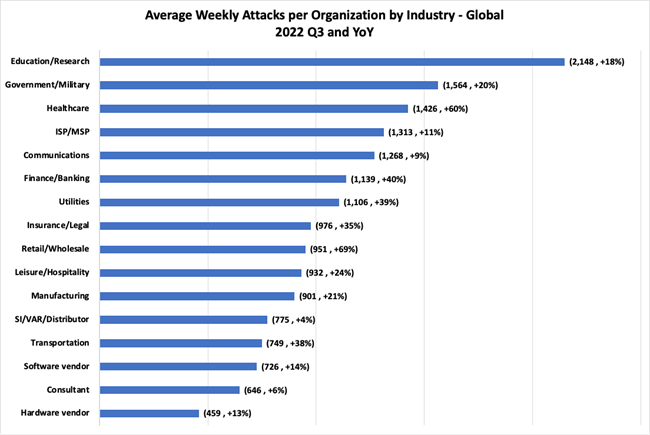
Check Point Research Third Quarter Of 2022 Reveals Increase In Cyberattacks And Unexpected Developments In Global Trends Check Point Software
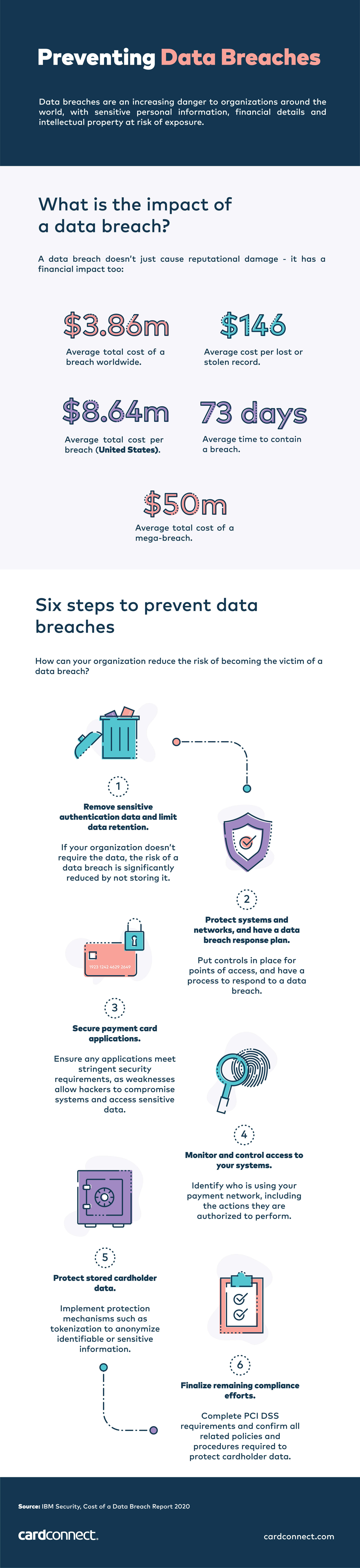
Data Breach Prevention Lessons For Pos Software Cardconnect

Which Of The Following Are Breach Prevention Best Practices Public Health

6 Most Common Causes Of Data Leaks In 2022 Upguard
![]()
How To Quantify The Cost Of A Data Breach A Case Study
5 Best Practices For Data Breach Prevention Endpoint Protector

Principle Of Least Privilege Cycode

Top 14 Data Security Best Practices
16 Best Data Loss Prevention Software Tools 2022 Free Paid
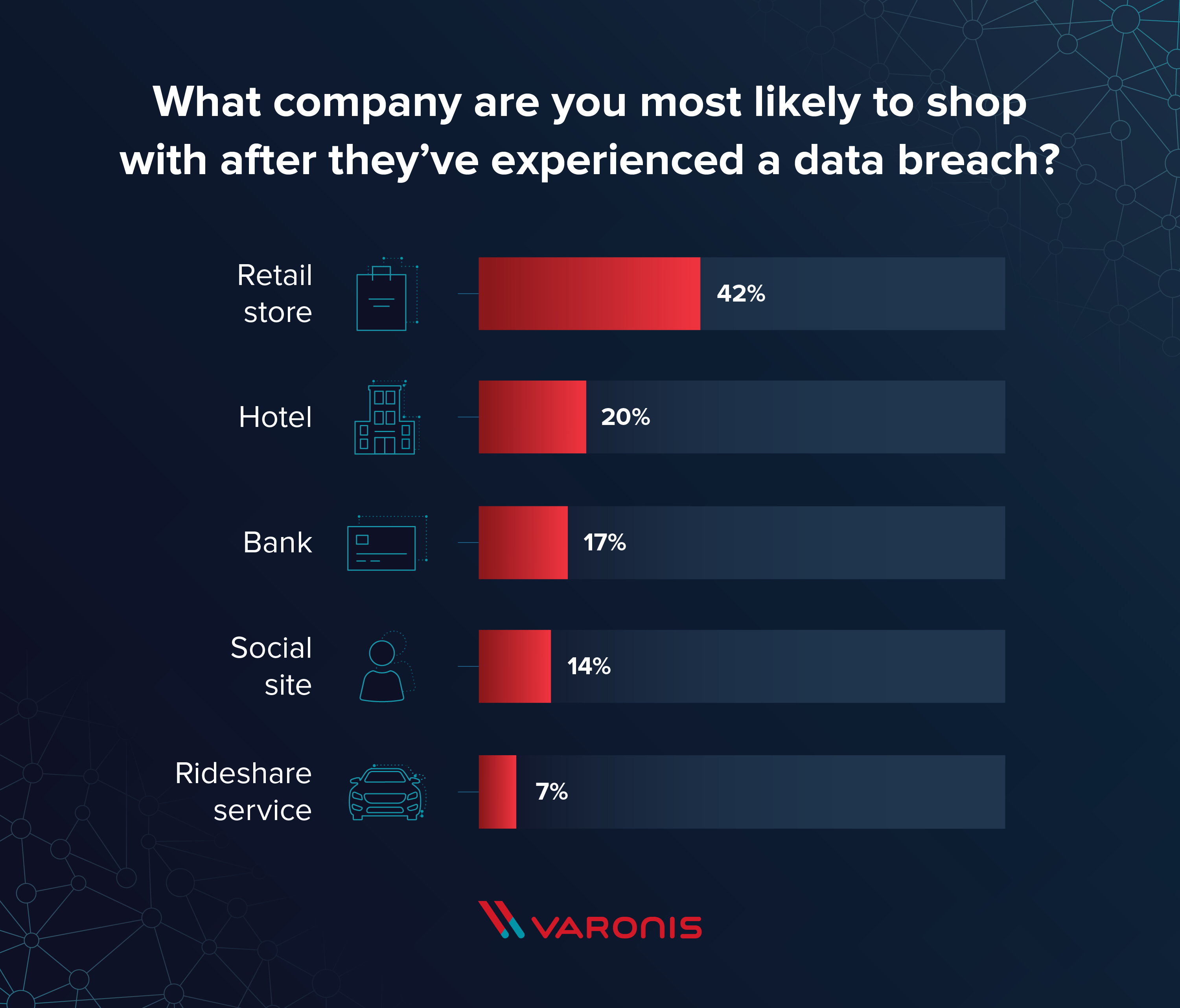
Analyzing Company Reputation After A Data Breach

Microsoft Office 365 Security Best Practices And Recommendations Pratum

Cybersecurity Best Practices For 2022 15 Data Protection Methods Ekran System

